I often get into discussions about budgets and how much a company should invest in its security program. There is no easy answer because the problem we are trying to solve has many unknowns.
There are many ways one may address this question, the main one being a rule of thumb.
The 10% rule
If Cyber Security budget is part of overall IT budget, it should be at least 10%
What is that 10%?
If you don't know what you need, if you are unclear about the environment, if you need to provide something quickly, if it's your first security budget, just start with what others are doing. And that is clear: 10% is the baseline today.
Hiscox Cyber Readiness report identifies a 10% on average, across several countries and industries.
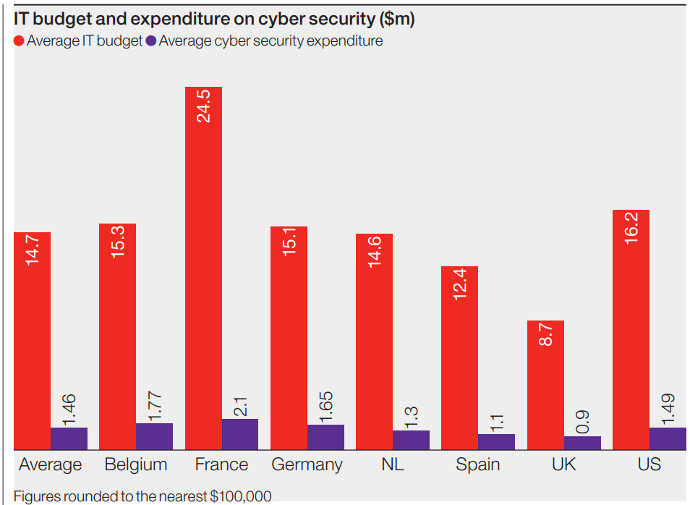 Ponemon Institute's report for Thales in 2018 indicated that 10% was the right number in 2015; with an upward trend.
Ponemon Institute's report for Thales in 2018 indicated that 10% was the right number in 2015; with an upward trend.
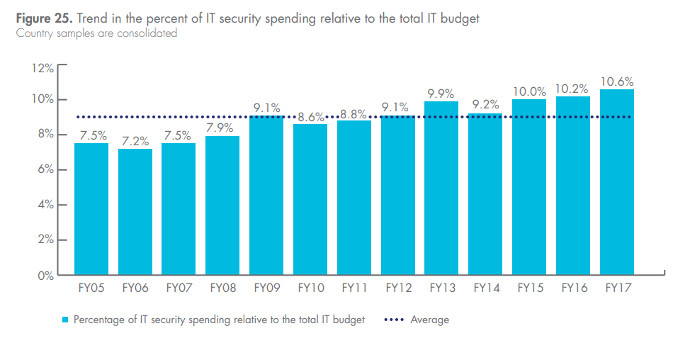
So is 10% enough?
There is at least one problem with this approach.
Considering Cyber Security, a risk-based function, as part of the IT, an operations-based function, and linking budgets generates a very wrong perspective. In the last 10 years organizational and technological developments have totally changed the digital and IT landscape of companies. The threat and attack surface change as well, following this transformation. Organizations are moving to the cloud frantically, tearing down their datacenters. The concept of "we need X firewalls to protect 10X datacenters" doesn't hold any more. Companies do not pay for firewalls as much and I'm surprised that companies still pay for (plain signature-based) Antivirus products at all. We can attribute both to old, outdated and inefficient requirements from regulatory bodies. But back to the issue at hand: The shift of the "security perimeter" from a physically defined perimeter to the end user device and user identity, as well as architectural changes such as zero-trust networks, means that the traditional security controls are not as effective and any assumptions made in the past about budget split have to be reconsidered.
The most clear proof for why this is wrong comes from the IT software vendors. Take Google's G Suite for example : The main difference between the Home and Business packages is on security, yet the price doubles. And that's nothing compared to the gap between Business and Enterprise, where the only real differentiation is security. The price doubles once again!
Office 365 enterprise plans have a similar (but not as big) gap. Office 365 E5 is 75% more expensive than E3, offering only advanced security, analytics, and voice capabilities. We could argue to what extent this price gap comes from security and how much comes from the other functionality but it won't help; I believe we will agree that security value is more than 10% of the whole.
If traditional IT software vendors raise their prices by more than 10% when they offer security on top, shouldn't we expect IT budgets to allocate an equivalent amount directly to security? If your answer to that question is "Yes", then you will see that 10% is far from the correct number and defining Cyber Security budget as part of the total IT may require a fresh start.
Current versus future view
There is another problem with this approach of 10%. It shows us what the current situation is, but not what is really needed from the investment and defence perspective. The current situation is that we have thousands of breaches every year, with billions of user records affected. If that is the way we want to go forward, then by all means let's not change the current security strategies, including investments.
Varonis estimated that cybersecurity budgets in 2019 are expected to reach $124 billion while the cybersecurity impact in 2018 was $1.5 trillion. I see a disproportionality here.
The workforce parameter
Have you heard about the fight for talent and the lack of cyber security personnel? Yes, me too and I don't believe the numbers are so bad - but they are bad. In any case, that situation bumps the salaries up. Although in my perspective they are not bumped enough considering the toll the situation has on employees' mental health and well - being, this is not the point I want to make. The point is that you should expect your security personnel to be among the most expensive in your IT department (if it is part of your IT department of course). One more thing to take into account when you budget your security investments; proper security personnel will be more expensive than standard IT personnel of the same seniority, so their 'share' of the total salary expenditure will be higher.
Organization-tailored approaches
Instead of relying on what others are doing, and instead of setting a flat 10% security budget target, companies should adopt an approach that matches their needs at the particular time. I personally expect that the budget will always be more than 10% if you follow any of these approaches but you will only know if you run the exercise.
Maturity based approach
The easiest way to move forward is the maturity based approach. Organizations should hire an experienced CISO or engage a respected Security consulting company (or both, of course), to identify the level of protection the company would need, and build the appropriate capabilities. If for example your organization has public servers needed for its operation, you should budget for penetration testing - no questions asked.
Advantage of this method is that if you're building something from scratch this is highly effective. You probably don't have visibility and don't have risk scenarios to do otherwise, so start by providing a minimum set of capabilities to the organization.
The problem with that approach is that either you’ll do the minimum, or you may spend money to initiatives that do not provide the best security posture improvement - and that is why an experienced CISO is your best bet here.
Risk based approach
Although the maturity based approach works nicely in organizations with no or very limited security, everybody should try to eventually move to a Risk based approach. One of the obvious benefits is that you can discuss with the organization about impact on business targets and management of business risks instead of just tools and processes that you want to implement. Importantly, that approach not only provides business alignment and allows you to enable the business, but is also more cost effective; you have the opportunity to direct the investments to what the organization really needs. No reason to buy firewalls for your offices any more, if you have no servers there; just switch to a cloud firewall / proxy and get done with it!
On the disadvantages of this method I would consider that it focuses mainly on protection and recovery, because they can be better linked to a risk mitigation. But what about detection and what about identification? How can one justify proper asset management on a risk based approach? I have heard people explaining the whole path of how not knowing that an asset exists (or its status) means you don't know if it gets protected and you won't know if it gets infected and... All is valid, but it's not a discussion that can be part of risk - management with executives; it gets too technical and too detailed.
For these basics I prefer to go with the maturity based approach.
Conclusion
So, overall my suggestions would be:
- if you have no experience or you need to argue budget in a conservative organization, go with the 10% rule
- if you are starting today from scratch, start with a maturity-based approach to deploy the basics (e.g. CIS top 20 controls)
- if you already have some security capabilities and visibility, take a risk-based approach to direct investments where focus is needed.
Thoughts?
